PR with payloads
Edit: Following the suggestions in our last ecosystem call, this Permission Update Request was divided into two:
PUR #8 - Permissions for Arbitrum and Gnosis Chain
PUR#9 - Permissions for ETH Mainnet
This action was taken to expedite the release of the already reviewed permissions. No changes were made to the requested permissions.
The following text reflects these changes, and the ETH Mainnet Permission Update Requests will be shared in a new post, where their review will continue.
Abstract
This proposal requests BalancerDAO’s approval for updates and new actions to the permissions policy governing the kpk-managed treasuries on Arbitrum, and Gnosis Chain.
The proposed changes expand the existing permissions to include new strategies, protocols, swaps, and bridging routes, while removing obsolete or deprecated contracts and interactions. They also streamline kpk’s fee-collection process and revoke the delegation’s permissions from the Zodiac Roles Modifier, as outlined in BIP-890.
The additional permissions focus on strategies that aim to increase the treasury’s risk-adjusted yield without introducing material new risk vectors to the current allocation. These include allocations to Aave Umbrella, Ethena, Spark, Resolv, new markets on Compound as well as kpk-curated vaults on Morpho and curated markets on Gearbox, among others.
Motivation
Treasury management must evolve in line with market conditions and protocol developments, including migrations, new pool launches, and improved access to financial instruments. Protocols and pools previously assessed as too immature or risky for BalancerDAO may become viable over time as they demonstrate reliability, liquidity, and operational robustness.
The proposed additions will allow kpk to implement advanced investment strategies such as delta-neutral stablecoin exposure, curated vaults, and the upgraded version of the Aave safety module, while deprecating outdated or higher-risk contracts.
Changes to the Permissions Policy
This proposal outlines the following modifications to the permissions policy:
Gnosis Chain:
- Bridge:
- Omnibridge:
- Update and addition of bridging routes from Gnosis Chain to Mainnet (same as above)
- Omnibridge:
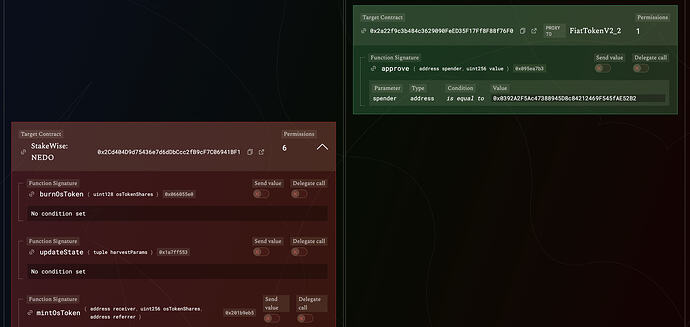
- Stakewise: removal of SeedNode vault (deprecated)
Arbitrum:
- Morpho: deposit and withdrawal into - kpk - USDC Yield
- Balancer v2: withdrawal permissions for Balancer BAL - axBAL
- Swaps (Cow Swap):
- COW, ARB <> USDC/ETH/WETH/ sUSDE/USDE
- USDC, USDT, USDE, sUSDE <> USDC, USDT, USDE, sUSDE
- WETH, wstETH, ETH <> WETH, wstETH, ETH
- ARB <> USDC, ETH, WETH
Zodiac Roles Modifier Permissions Policy
Permissions page
Gnosis Chain: link here
Arbitrum: link here
Permissions diff page
Gnosis Chain: link here
Arbitrum: link here